Cyber Shield: The Dawn of Digital Resilience with CRA
.jpg?width=762&height=762&name=Cyber%20Shield%20The%20Dawn%20of%20Digital%20Resilience%20with%20Cyber%20Resilience%20Act%20(CRA).jpg)
In an era where digital frontiers are expanding at an unprecedented pace, the Cyber Resilience Act (CRA) emerges as a beacon of security in the tumultuous seas of cyberspace. This groundbreaking legislation, proposed by the European Union, is not just a set of guidelines; it’s a robust shield designed to fortify every digital product against the relentless onslaught of cyber threats. From baby-monitors to smart-watches, products and software that contain a digital component are omnipresent in our daily lives. Less apparent to many users is the security risk such products and software may present.
At its core, the CRA is a visionary blueprint for a safer digital tomorrow. It mandates a new standard of cybersecurity for all products with digital elements, ensuring that from the smallest app to the largest network, every byte is safeguarded with the highest level of security. The CRA is not merely a policy; it’s a promise - a promise of resilience, reliability, and a steadfast commitment to protecting the digital integrity of individuals and enterprises alike.
The Imperative for Cyber Resilience Act in Today’s Connected World
As our lives become more intertwined with digital products, the risk of cyber-attacks grows. The Cyber Resilience Act (CRA) is a pivotal piece of legislation that addresses the urgent need for enhanced cybersecurity in an increasingly digital world. According to the EU's Digital Strategy the problem addressed by the CRA is two-fold.
- First is the inadequate level of cybersecurity inherent in many products, or inadequate security updates to such products and software.
- Second is the inability of consumers and businesses to currently determine which products are cybersecure, or to set them up in a way that ensures their cybersecurity is protected.
CRA will guarantee:
- Harmonized rules when bringing to market products or software with a digital component.
- A framework of cybersecurity requirements governing the planning, design, development and maintenance of such products, with obligations to be met at every stage of the value chain.
- An obligation to provide duty of care for the entire lifecycle of such products.
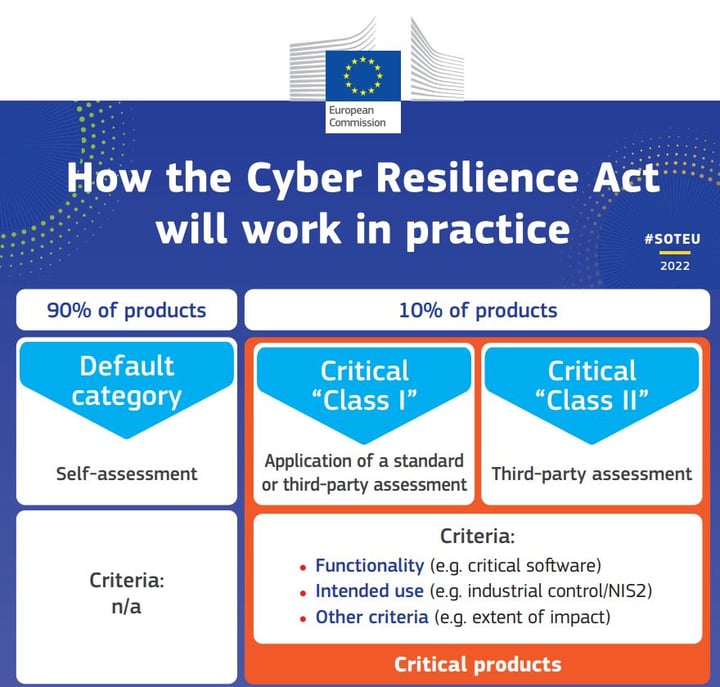
Here’s how it will work in practice
CRA will create harmonized rules, improve cybersecurity, and empower users to make safer choices when using digital products by having:
Mandatory Cybersecurity Requirements
- The CRA will introduce mandatory cybersecurity requirements for products with digital elements. Manufacturers and retailers of such products will need to comply with these standards.
- These requirements will govern the planning, design, development, and maintenance of digital products throughout their lifecycle.
CE Marking
- When the Regulation enters into force, software and products connected to the internet will bear the CE marking to indicate compliance with the new standards.
- This marking will empower consumers and businesses to make informed choices, confident in the cybersecurity credentials of CE-marked products.
Coverage and Exclusions
- The CRA applies to all products connected directly or indirectly to another device or network, except for specified exclusions (e.g., open-source software, medical devices, aviation, and cars).
- Manufacturers will have to apply the rules 36 months after their entry into force.
Ongoing Review
- The Commission will periodically review the Act and report on its functioning.
- By prioritizing cybersecurity, the CRA aims to safeguard consumers and businesses from inadequate security features and ensure better protection against cyber risks.
Unveiling the CRA’s Product Classifications
The Cyber Resilience Act (CRA) classifies products with digital elements into different categories to address their cybersecurity requirements. Here are the classifications:
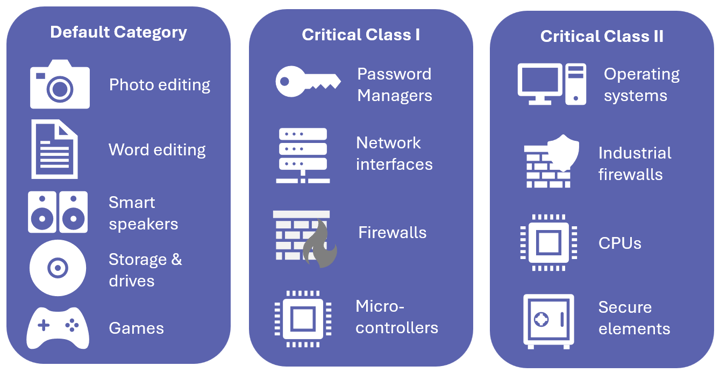
Class I
- Includes products such as Internet browsers, antivirus programs, password managers, and VPNs.
- These are essential tools used by individuals and businesses for secure online activities.
Class II
- Encompasses products like card readers, desktops, mobile terminals, and devices relying on the Internet of Things (IoT).
- Class II products face more stringent cybersecurity requirements due to their critical role in various contexts.
Unclassified or Default Category
- Some products may not fall into the specific Class I or Class II categories.
- These unclassified products still need to meet baseline cybersecurity standards under the CRA.
In summary, the CRA’s classification system ensures that products with digital elements receive appropriate cybersecurity measures based on their criticality and functionality.
<Source: European Cyber Resilience Act (CRA)>
Examples of CRA Classification
Below is a list of product examples by their classification:
Navigating the Minefield: The High Stakes of Ignoring the Cyber Resilience Act
The Cyber Resilience Act (CRA) carries significant consequences for non-compliance in the form of severe financial repercussions and impact on the security of digital products within the EU market.
Penalties and Fines
- Organizations failing to adhere to essential cybersecurity requirements under the CRA can face substantial fines.
- The administrative fines can be up to €15 million or 2.5% of the offender’s total worldwide annual turnover for the preceding financial year, whichever is higher.
- These penalties apply to manufacturers, importers, and distributors of products with digital elements (PDEs) placed on the EU market.
Enforcement Timeline
- Much of the CRA becomes enforceable approximately three years after enactment, around February 2027.
- Security vulnerability and cyber incident reporting requirements apply in less than two years after enactment, around November 2025.
- Provisions related to conformity assessment bodies apply approximately 18 months after enactment, around August 2025.
Synergizing Security: The Confluence of CRA and NIS2 in Strengthening OT Cyber Resilience

In the intricate web of modern cybersecurity, two legislative titans stand out for their pivotal roles in safeguarding Europe’s digital infrastructure: the Cyber Resilience Act (CRA) and the Network and Information Systems Directive (NIS2). While each serves a distinct purpose, their convergence in the Operational Technology (OT) space forms a formidable alliance against cyber threats. If you would like to know more about it, please read A Comprehensive Guide to NIS2 Compliance and Operational Technology Resilience.
The CRA, with its focus on products with digital elements, ensures that devices and software integral to OT environments meet stringent cybersecurity standards. It mandates that manufacturers embed resilience into the DNA of their products, thereby fortifying the first line of defense against cyber incursions.
NIS2, on the other hand, casts a wider net, encompassing the security of network and information systems, particularly those deemed essential for societal and economic well-being. It calls for robust risk management measures and swift incident reporting, which are critical in OT settings where a cyberattack can have immediate physical repercussions.
Together, the CRA and NIS2 create a layered security strategy. The CRA’s product-centric approach ensures that each component within an OT environment is inherently secure, while NIS2’s systemic perspective ensures that these components interact within a secure framework. This dual approach not only enhances the security of individual devices but also fortifies the entire OT ecosystem.
Summary
In the digital tapestry of our modern lives, the fabric of security is often stretched thin by the relentless assault of cyber threats. It mandates that all digital products, from the ubiquitous smartphone to the most sophisticated Internet of Things (IoT) device, adhere to rigorous cybersecurity standards. This act ensures that resilience is not an afterthought but a fundamental criterion from the inception of a product’s design to its final deployment.
For consumers, the CRA is a silent guardian. It empowers them with the assurance that the digital tools and services they rely on are not just functional but fortified against cyber incursions. The act also introduces a clear and recognizable sign of security—the CE marking—guiding consumers towards safer digital choices.
In summary, the CRA is a clarion call for a unified front against cyber threats. It is a strategic move to elevate the standards of cybersecurity, safeguard personal data, and foster a resilient digital economy. As we navigate through the complexities of the cyber world, the CRA stands as a bulwark, ensuring that Europe’s digital future is secure and resilient.
--------------------

Author: Vinny Sagar, Solution Architect, swIDch
With over 15 years of experience in pre-sales, consulting and software development in the Identity and Cyber Security space Vinny has helped many clients across various industries and regions to design and deploy Zero Trust solutions that meet their specific needs and challenges.
--------------------

swIDch will continue its quest to innovate and pioneer next-generation authentication solutions. To stay up-to-date with the latest trends sign up to our newsletter and check out our latest solutions.

The distributed control system (DCS) is the core of industrial automation. It synchronises critical operations in power

In the age of digital transformation, cybersecurity has become a boardroom topic across industries. But while IT

The ubiquity of Public Key Infrastructure (PKI) in securing our digital world is undeniable. From the padlock icon in
Looking to stay up-to-date with our latest news?