A Comprehensive Guide to NIS2 Compliance and OT Resilience

The NIS2 Directive is the EU-wide legislation on cybersecurity. It provides legal measures to boost the overall level of cybersecurity in the EU. The EU's NIS2 Directive has arrived, bringing stricter cybersecurity regulations to vital sectors like energy, water, and transportation. Operational Technology (OT) systems, the backbone of our critical infrastructure, are now under the spotlight, requiring organizations to ramp up their security posture to ensure the continued operation of essential services. I will delve into the intricacies of NIS2 compliance in the OT realm, exploring the challenges and opportunities, and introducing innovative solutions on the path to a secure and compliant OT environment.The EU cybersecurity rules introduced in 2016 were updated by the NIS2 Directive in 2022 and all applicable organizations and companies have until 2024 to comply with the new legal requirements after which they will be eligible for potential fines. It modernized the existing legal framework to keep up with increased digitisation and an evolving cybersecurity threat landscape. By expanding the scope of the cybersecurity rules to new sectors and entities, it further improves the resilience and incident response capacities of public and private entities, competent authorities and the EU as a whole.
Who does it impact?
NIS2 impacts a wide range of entities that provide essential or important services to the European economy and society, such as transport, energy, health, banking, digital infrastructure, cloud computing, online marketplaces, and more. The NIS2 Directive applies to both medium and large companies based within an EU member state, as well as smaller companies that provide trust services. These entities must comply with the security measures and reporting obligations under the NIS2 Directive, and may face sanctions or audits if they fail to do so. NIS2 also affects the supply chains and service providers of these entities, as they must ensure the security of their network and information systems as well.
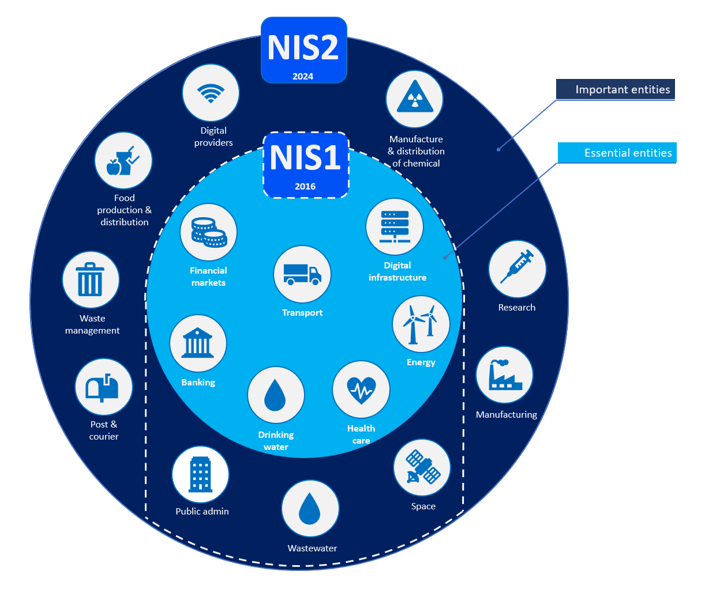
The diagram above shows the expanded scope of NIS2 compared to NIS1 and the important and essential entities it covers.
What are the expectations NIS2 places on organizations?
The NIS2 Directive places various requirements on organizations that provide essential or important services to the EU, such as risk management, corporate accountability, reporting obligations, and business continuity. Additionally, the NIS2 Directive mandates that these organizations implement 10 minimum security measures to address specific forms of cyberthreats, such as incident handling, supply chain security, vulnerability handling and disclosure, cryptography and encryption, and multi-factor authentication. These requirements aim to enhance the cyber resilience of network and information systems across the EU and protect them from incidents that could have significant impact on the economy and society.
.png?width=720&height=504&name=NIS2%20in%20Operational%20Technology%20(OT).png)
NIS2 10 Minimum Measures
In addition to the four overarching areas of requirement, NIS2 mandates that essential and important entities implement baseline security measures to address specific forms of likely cyberthreats. These include
- Risk assessments and security policies for information systems
- Policies and procedures for evaluating the effectiveness of security measures.
- Policies and procedures for the use of cryptography and, when relevant, encryption.
- A plan for handling security incidents
- Security around the procurement of systems and the development and operation of systems. This means having policies for handling and reporting vulnerabilities.
- Cybersecurity training and a practice for basic computer hygiene.
- Security procedures for employees with access to sensitive or important data, including policies for data access. Affected organizations must also have an overview of all relevant assets and ensure that they are properly utilized and handled.
- A plan for managing business operations during and after a security incident. This means that backups must be up to date. There must also be a plan for ensuring access to IT systems and their operating functions during and after a security incident.
- The use of multi-factor authentication, continuous authentication solutions, voice, video, and text encryption, and encrypted internal emergency communication, when appropriate.
- Security around supply chains and the relationship between the company and direct supplier. Companies must choose security measures that fit the vulnerabilities of each direct supplier. And then companies must assess the overall security level for all suppliers.
NIS2 in Operational Technology (OT)
As critical infrastructure industries such as power, water, transport are vital lifelines in our modern world maintain reliable operation despite depending on network and information systems, including operational technology (OT) that have been the main target of recent cyber attacks.
NIS2 can be applied to OT environments by following the security measures and reporting obligations specified in the directive, as well as the best practices and guidelines from relevant authorities and standards.
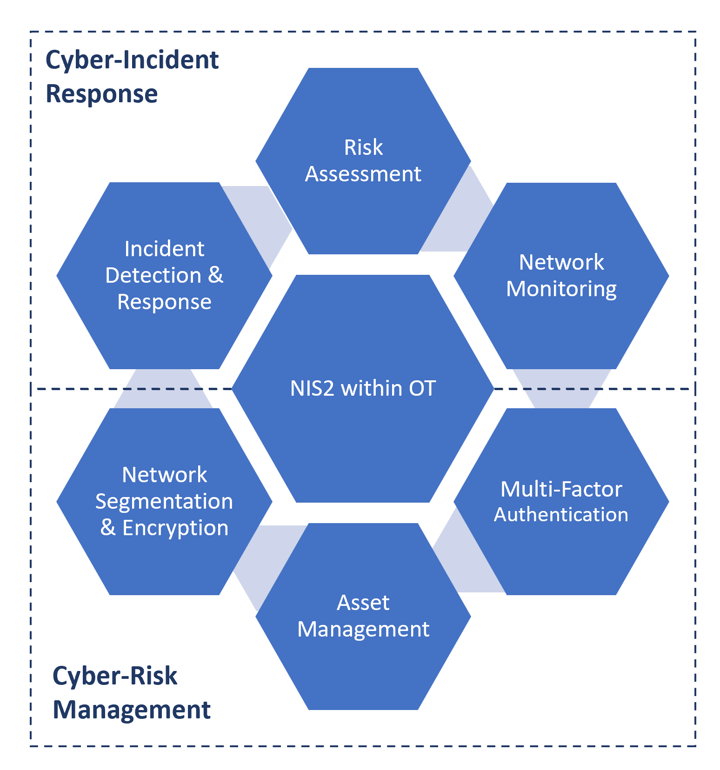
The updated NIS Directive provides requirements to create a cybersecurity program based on strengthening cyber-risk management and cyber-incident response. These two pillars of security address an organization’s capabilities of measuring its cybersecurity posture and recovering from an incident. For OT, both of these concepts require understanding the industrial environment, protecting critical assets, and monitoring for malicious communications.
Risk Assessment
Conduct a comprehensive risk assessment of the network and information systems, including OT and identify the potential impact of cyber incidents on the essential or important services provided. Risk assessments effectively answer the question “What does a really bad day look like, and what is the potential of it happening based on the resilience of our OT infrastructure?”. Within OT, risk evaluation should be based on the industrial process at each entity and the uniqueness of the system architecture.
Network Monitoring
Monitor the network and information systems, including OT and ICS, for any signs of cyber threats or anomalies, and use tools and solutions that can provide visibility and protection across the OT and IT domains. A proactive approach to log centralization for monitoring can help ease the burden when an incident response team attempts to identify the root cause of an event.
Incident Detection & Response
Report any significant or substantial cyber incidents to the competent national authorities within 24 hours, and cooperate with them to resolve the incidents and mitigate the impact. Review and update the security measures and reporting procedures regularly, and ensure they are aligned with the latest NIS2 requirements and best practices.
Network Segmentation & Encryption
Entities should rely on strong network perimeters by segmenting critical OT networks from corporate communications. An OT network segment should also leverage an ICS DMZ and an architecture. Policies and procedures should be in place to use of cryptography and, when relevant, encryption.
Asset Management
Asset management is the discipline of understanding the devices within a network. A robust NIS2 program has a current inventory, including important parameters for securing those devices, such as associated software and firmware versions, known security controls, and criticality of the asset itself.
Multi-Factor Authentication
A variety of ICS devices have default and/or hardcoded passwords used by vendors and maintenance technicians that add complexity to any access control management program, which is an important consideration for NIS2 security policies and supply chain risk management elements. The use of multi-factor authentication, continuous authentication solutions, and encrypted internal emergency communication must be considered.
How swIDch can help achieve NIS2 compliance?
swIDch's OTAC technology is a patented algorithm that generates a one-time dynamic authentication code that can identify and authenticate users in a networkless environment. This technology can be used in the OT environment to achieve NIS2 compliance by:
- Providing a secure and convenient way to access OT and ICS systems without relying on static information, such as passwords, or PINs, that are vulnerable to cyberattacks.
- Reducing the complexity and friction of the authentication process by combining user identification and authentication steps into a single code, which can be generated on any device, such as a smartphone, tablet, or smartcards.
- Enhancing the resilience and availability of OT and ICS systems by enabling offline authentication, which does not depend on network connectivity or server communication.
- Supporting the implementation of the 10 minimum security measures required by NIS2, such as incident handling, supply chain security, cryptography and encryption, and multi-factor authentication.
swIDch's OTAC technology is a innovative and agile solution that can help organizations that provide essential or important services to the EU to comply with NIS2 and protect their OT and ICS environments from cyber threats. swIDch’s OTAC provides a highly optimized and highly secure authentication solution specifically for PLC devices. It utilizes our dynamic 'one-time authentication code' (OTAC) technology to resolve typical ICS/OT security challenges.
OTAC resolves:
- Password sharing in password-only authentication systems
- Difficulty managing ID/PW specified for each PLC device
- Difficulty managing user changes (leavers / contractors etc)
- Hacking attempts using password cracking software
OTAC ensures only known and authorized users/devices can access PLC using dynamic, non-reusable, constantly changing code guaranteed with 0% duplicates (defeats packet sniffing attacks)
Conclusion
The NIS2 Directive is a comprehensive and ambitious regulation that aims to improve the cyber security and resilience of network and information systems across the EU. It applies to a wide range of entities that provide essential or important services, such as transport, energy, health, banking, digital infrastructure, cloud computing, online marketplaces, and more.
One of the key challenges for these entities is to ensure the security and availability of their operational technology (OT) and industrial control systems (ICS), which are critical for the delivery of their services. OT and ICS systems are often exposed to cyber risks due to their legacy, heterogeneous, and complex nature, as well as their increasing connectivity and interdependence with information technology (IT) systems. Therefore, these entities need to adopt solutions and practices that can protect their OT and ICS systems from unauthorized access, manipulation, or disruption.
By using swIDch’s OTAC technology, entities that provide essential or important services to the EU can comply with NIS2 and protect their OT and ICS environments from cyber threats. swIDch’s OTAC technology is an agile and flexible solution that can adapt to the changing needs and challenges of the OT and ICS domain. It can also help these entities gain trust and confidence from their customers and stakeholders, as well as a competitive edge in the market. swIDch’s OTAC technology is the future of OT and ICS security and resilience.
--------------------

Author: Vinny Sagar, Solution Architect, swIDch
With over 15 years of experience in pre-sales, consulting and software development in the Identity and Cyber Security space Vinny has helped many clients across various industries and regions to design and deploy Zero Trust solutions that meet their specific needs and challenges.
--------------------

swIDch will continue its quest to innovate and pioneer next-generation authentication solutions. To stay up-to-date with the latest trends sign up to our newsletter and check out our latest solutions.

The distributed control system (DCS) is the core of industrial automation. It synchronises critical operations in power

In the age of digital transformation, cybersecurity has become a boardroom topic across industries. But while IT

The ubiquity of Public Key Infrastructure (PKI) in securing our digital world is undeniable. From the padlock icon in
Looking to stay up-to-date with our latest news?