

PLC OTAC
Single-step MFA using our OTAC technology allows manufacturers and operators to
significantly increase security with minimal disruption and minimal computing requirements
whilst removing vulnerabilities and greatly simplifying the authentication process.
Pain points
As industrial automation advances, integrating Operational Technology (OT) and Information Technology (IT) requires stronger authentication systems. The rise in PLC use, projected to hit $22.17 billion by 2030, highlights the need to protect OT and PLCs from unauthorized access, as seen in notable cyberattacks on water treatment systems.
Current PLC systems often rely on password-based authentication due to limited computing power, resulting in significant vulnerabilities. Common challenges include:
⚠️Weak authentication in current PLC systems
Industrial Control Systems (ICSs) often face limitations in adopting advanced security measures due to their low computing power, leading to a reliance on password-based credentials for authentication. While these passwords are widely used, they come with a host of significant challenges that can jeopardize security.
- Manufacturer default passwords still in use
- Shared passwords, leading to weak user identification
- Difficulties in managing passwords for multiple PLC devices
- Managing user access during personnel changes
- Password vulnerabilities to brute force, phishing, and credential attacks
These weaknesses were evident in the Stuxnet attack, which targeted poorly configured passwords and remains a risk.

⚠️Regulatory Compliance Challenges in OT Security
As the regulatory landscape for Operational Technology (OT) continues to evolve, companies are increasingly required to comply with frameworks such as the NIS2 directive, the Cyber Resilience Act (CRA), and IEC 62443 standards. These regulations impose stricter cybersecurity requirements for critical infrastructure sectors, including energy, water, and transportation, to protect against cyberattacks. Non-compliance can lead to significant repercussions such as financial penalties, reputational damage, or even service disruptions.
Many organizations face challenges in adapting their legacy OT systems, which were not originally designed with such stringent security controls in mind. This is particularly true for Programmable Logic Controllers (PLCs), which are often low-power devices lacking the capability to support modern, resource-intensive security solutions.
- Meeting compliance standards for regulations like NIS2, CRA, and IEC 62443 requires more advanced security solutions than legacy OT systems can provide.
- Static password-based authentication often falls short of compliance requirements, as it is vulnerable to cyberattacks like password cracking, phishing, and brute force attacks.
- Legacy OT systems struggle to accommodate modern security solutions without extensive and costly upgrades.
- Failure to comply with these standards can lead to severe penalties, operational downtime, and even regulatory sanctions.
⚠️Deployment Issues with Multiple PLC Devices
In many industrial settings, end-users deploy PLCs from a range of manufacturers, each with its own unique set of protocols, security features, and communication standards. This diversity leads to fragmented security measures across the network, making it difficult to implement a consistent and unified security approach. As different PLCs may require distinct tools for monitoring and protection, the result is often a disjointed security system that leaves gaps in coverage. These inconsistencies create vulnerabilities, as attackers can target the weakest link in the system, exploiting areas where security features may be outdated, misconfigured, or incompatible with other devices in the network.
⚠️Limited Security Oversight Without Experts
PLCs are usually managed by control engineers whose primary focus is ensuring the functionality and performance of the systems, rather than cybersecurity. This setup often leads to a reliance on manufacturers or third-party vendors to provide security patches, updates, and safeguards, rather than having dedicated internal security teams handling these critical tasks. Unfortunately, without direct oversight from cybersecurity professionals, there can be significant blind spots in the overall protection strategy. Furthermore, the separation between operational and security teams can delay responses to incidents, further jeopardising the security of the entire OT infrastructure.
⚠️Challenges of Upgrading OT/PLC Systems
Upgrading OT systems, including PLCs, to meet modern security standards is often seen as a daunting and resource-intensive process. Many of these systems are integrated into essential, continuous operations, meaning any downtime for security upgrades can disrupt critical processes, leading to potential financial losses. As a result, companies may delay or even avoid necessary upgrades, leaving systems exposed to known vulnerabilities for extended periods. Additionally, the complexity of upgrading legacy systems, which were not designed with modern cybersecurity threats in mind, can require specialised knowledge and resources.
⚠️Common Vulnerabilities Across RTUs, SCADAs, & HMIs
In OT environments, devices like Remote Terminal Units (RTUs), Supervisory Control and Data Acquisition (SCADA) systems, and Human-Machine Interfaces (HMIs) share similar vulnerabilities to PLCs. They often operate with weak or default passwords, outdated security protocols, and are exposed to network-based threats. These devices are critical in controlling and monitoring essential processes but are often left unsecured due to the complexity of updating their systems in real-time operations. As a result, they become easy targets for cyberattacks, putting entire industrial operations at risk.
The Solution
swIDch's PLC OTAC effectively addresses the challenges faced by Industrial Control Systems (ICS) and Operational Technology (OT) environments. Utilizing the world’s first one-way dynamic authentication (OTAC) technology, it delivers high security with minimal resource requirements. OTAC can be deployed in various modes, providing passwordless multi-factor authentication (MFA) without network dependency. Unlike other security solutions that add complexity and user friction, OTAC streamlines the login process. Users don’t need to remember usernames or passwords, offering a single-step MFA for a seamless experience.

🔎Achieving Compliance in OT Cybersecurity Frameworks
swIDch’s PLC OTAC (Programmable Logic Controller One-Time Authentication Code) solution ensures organizations meet regulatory standards like NIS2, CRA, and IEC 62443 through enhanced authentication mechanisms tailored for OT environments.
- NIS2 Compliance: Provides secure, passwordless access to OT systems, addressing vulnerabilities associated with static credentials and supporting the minimum security measures outlined by NIS2.
- CRA Compliance: Replaces traditional password-based systems with dynamic authentication codes, reducing risks from unauthorized access and simplifying the authentication process.
- IEC 62443 Compliance: Aligns with Identification and Authentication Control (FR1) by ensuring that only authorized users access PLCs through non-reusable, dynamic codes.
🔎Neutralising Password Vulnerabilities with Dynamic Authentication Codes
swIDch’s PLC OTAC provides a secure solution for PLC devices, using dynamic one-time authentication codes (OTAC) to tackle challenges like default passwords, user changes, and hacking vulnerabilities, ensuring only authorized access and protection against packet sniffing.
- OTAC ensures only known and authorised users/devices can access PLC using dynamic, non-reusable, constantly changing code guaranteed with 0% duplicates (defeats packet sniffing attacks)
Current PLC certification: Password-based
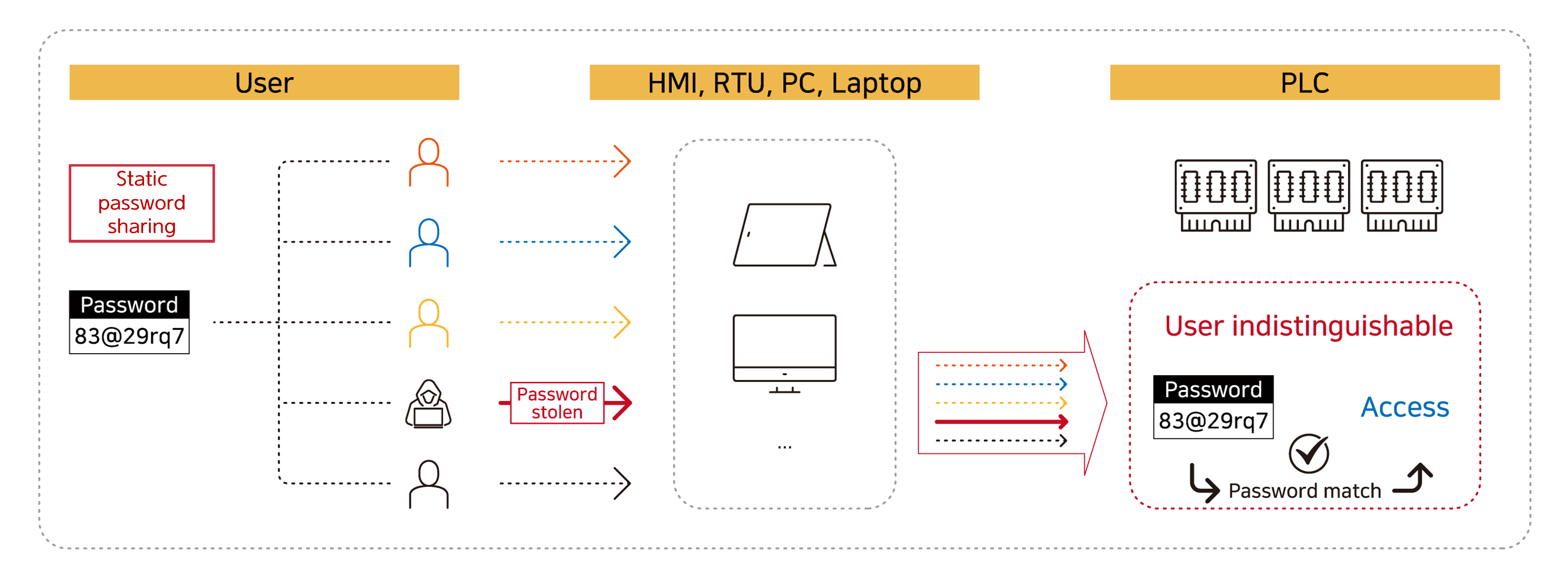
- Password sharing between engineers
- Access is granted to users who are indistinguishable (un-identified)
- If a password is stolen (from any user) it can be later used to gain access without any further challenge
Optimal PLC authentication method: OTAC-based authentication
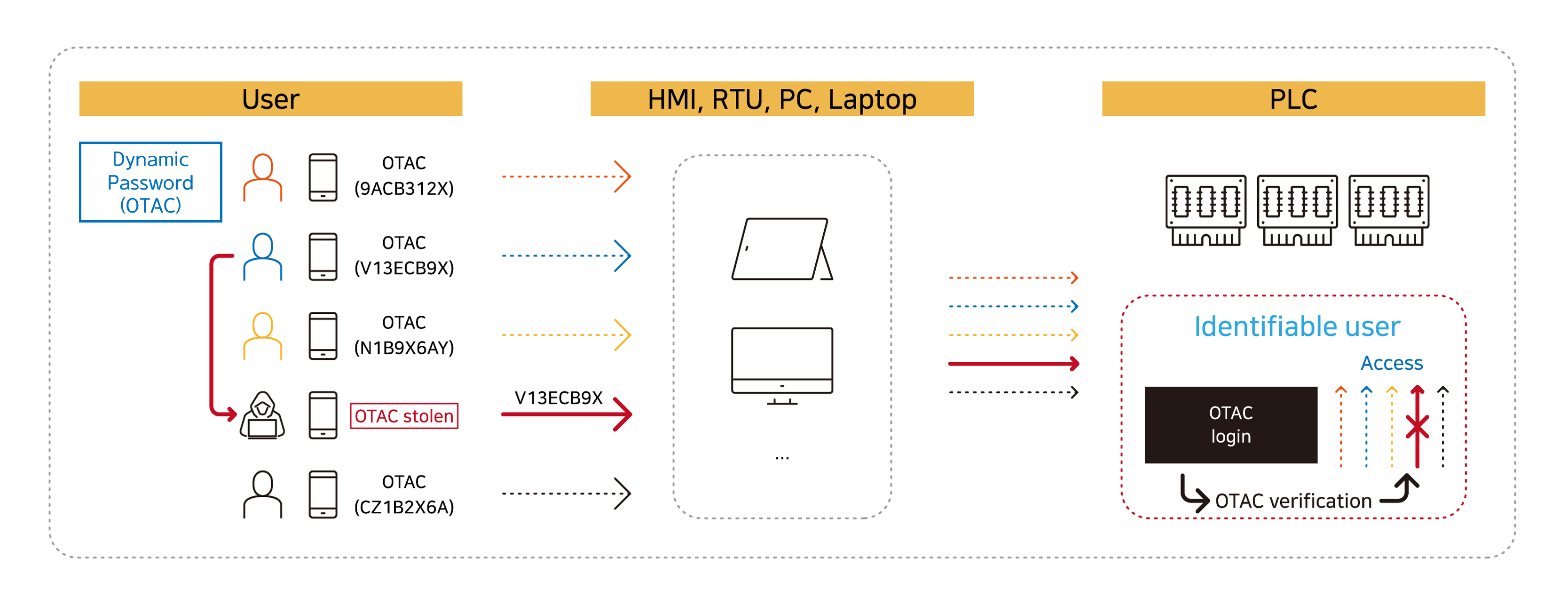
- No password sharing – users enter dynamic codes (OTAC) which are generated differently each time
- Access is only granted to authorised users – who are also fully identifiable
- If the OTAC is stolen and later used it will be denied access by the OTAC verification module
- All of this is possible without any need to modify the existing password interface (8-digit example above)
OTAC resolves Common Vulnerabilities and Exposures (CVE) including:
CVE-2022-32143, CVE-2022-2003, CVE-2022-1794, CVE-2021-37172, CVE-2021-32982, CVE-2021-32978, CVE-2021-20827, CVE-2020-15791, CVE-2020-10628, CVE-2020-10276, CVE-2022-2758
![[image1] PLCNext Store_OTAC auth_appstore screenshot_eng [image1] PLCNext Store_OTAC auth_appstore screenshot_eng](https://www.swidch.com/hs-fs/hubfs/%5Bimage1%5D%20PLCNext%20Store_OTAC%20auth_appstore%20screenshot_eng.jpg?width=2000&height=1124&name=%5Bimage1%5D%20PLCNext%20Store_OTAC%20auth_appstore%20screenshot_eng.jpg)
🔎Customisable Design for Each Company's Environment
PLC OTAC allows for easy deployment, accommodating the specific needs of each end-user. It supports various authentication code lengths and issuance mediums, such as smartphones or display cards, providing flexibility in implementation.
🔎Maintaining Existing UX/UI and Standardising Authentication Processes
swIDch ensures a seamless transition by allowing end-users to maintain existing PLC authentication UX/UI. Based on successful Proof of Concept (PoC) and Minimum Viable Product (MVP) implementations, it offers a standard process for device and user registration.
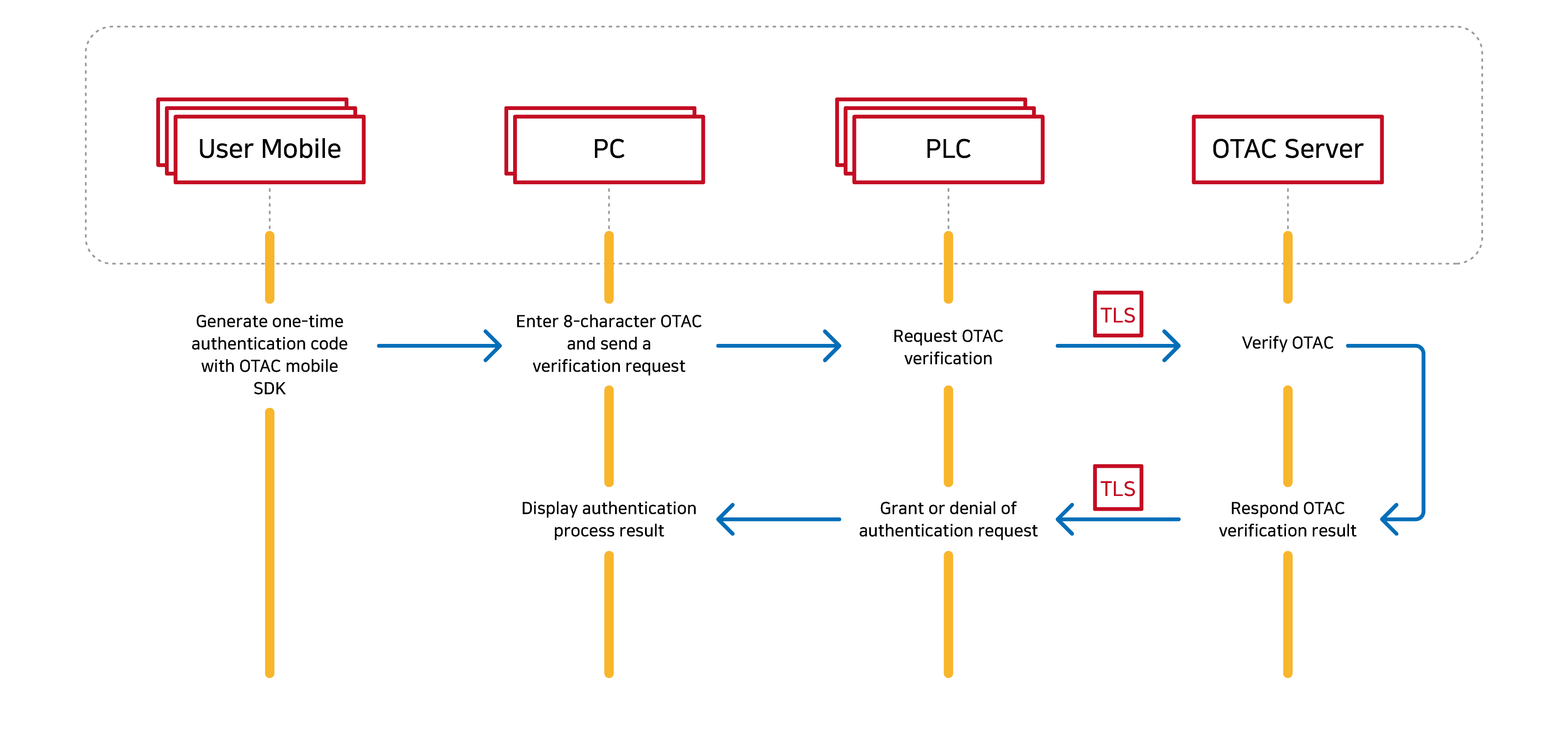
🔎Seamless Expandability to Secure All OT Devices
swIDch’s PLC OTAC solution addresses these pain points by delivering a scalable, dynamic authentication technology that goes beyond securing just PLCs. With its advanced one-time authentication codes (OTAC), swIDch can protect Remote Terminal Units (RTUs), Supervisory Control and Data Acquisition (SCADA) systems, Human-Machine Interfaces (HMIs), and other OT devices, ensuring that only authorized access is granted. This unified approach to device security provides real-time protection without requiring extensive infrastructure changes or complex configurations, effectively safeguarding the entire OT ecosystem from unauthorized access and cyber threats.
%20OTAC%20auth%20MFA%20Deployment%20Model.png)
Solution Deployment Examples in OT
In operational technology (OT) environments, adaptability is crucial. Our PLC OTAC solution offers flexible, configurable options for seamless integration, whether deployed on a standalone PLC, a central server, or a hybrid setup. Explore more about specific applications and deployment scenarios of PLC OTAC.
Learn More>
Benefits
swIDch’s PLC OTAC allows manufacturers and operators to significantly increase security with minimal disruption and minimal computing requirements whilst at the same time removing password associated vulnerabilities, and thus greatly simplifying the authentication process. Resolving PLC challenges opens the door to faster time-to-market for new products and solutions and therefore increased productivity and ultimately efficiency, a critical component of all ICS and OT systems.

Unique features of swIDch’s OTAC
- Uni-directional authentication (no network environment required)
- Lower CPU overhead (ie faster) compared to other authentication/encryption methods
- Unique dynamic code for each individual user - no more indistinguishable user access
- Highly configurable code parameters enabling deployment with minimal UI changes if required
- Lightweight SDK/applet available to implement code generator in multiple forms (eg users smartphone or NFC card)
💡Significant Savings on Manpower and Cost
PLC OTAC improves user authentication without the need for additional hardware specifications or network changes, reducing the cost and time required for a new authentication process.
💡Improved Productivity and Efficiency
With a compact algorithm code size, PLC OTAC allows for versatile implementations, requiring low CPU overhead. It adapts to existing infrastructure, eliminating the need for extensive changes and costly upgrades.
💡Easy Management Without Technical Barriers
OTAC-generated authentication codes simplify PLC access management, limiting access to authorised users and devices. The setup process is straightforward, enabling efficient management without requiring extensive technical expertise or training courses.

Contact us today
Why swIDch
that provides all of the following features, tested and substantiated
by the University of Surrey technical report
sufficient to IDENTIFY user
and AUTHENTICATION
off-the-network environment
Single-step identification and authentication with the code alone. Include our biometric option and get single-step MFA. Vastly improved UX by removing steps.
OTAC is a dynamic code, which means the code is constantly changing. Eliminates all use of static information. Forget usernames and passwords forever. Vastly reduced workload for IT helpdesks.
No network connection required for generating OTAC, enabling uninterrupted use no matter where you are. No more waiting for additional tokens/OTPs and no need for heavy public key infrastructure (PKI).
Highly configurable code parameters and lightweight SDK/applet means wide range of deployment options on many devices across multiple sectors.


