.jpg)

IoT Auth Platform OTAC
Enforce and maintain a more secure and accurate authentication
process with all IoT devices for businesses and homes.
Pain points
According to Statistica, the number of Internet of Things (IoT) devices worldwide is forecast to almost triple from 9.7 billion in 2020 to more than 29 billion IoT devices in 2030. This proliferation of IoT devices makes them easy targets for hacking and malware. In fact, 32% of the enterprises that have already adopted IoT consider data security issues related to the lack of skilled personnel to be the most critical concern for their IoT ecosystem.. Of course, various defense measures have emerged to prepare for these security threats, but there is a limit to encompassing low-cost, low-spec IoT devices.

IoT hacking problems exploding worldwide
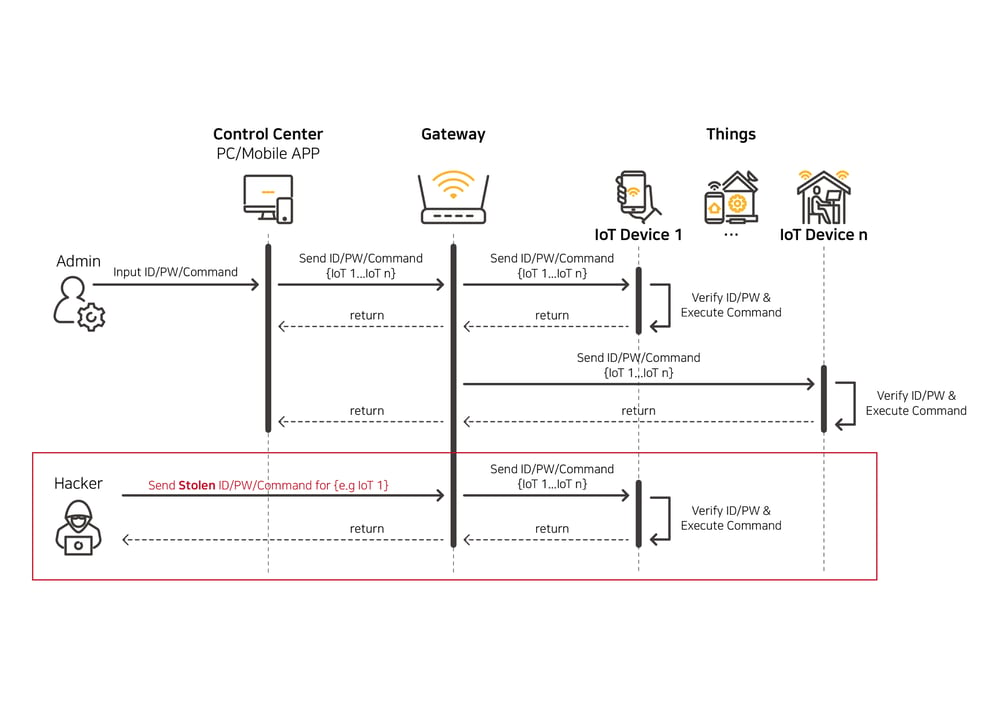
In 2021, a hacker group hacked a large amount of security camera footage collected by a Silicon Valley startup, accessed live feeds of 150,000 surveillance cameras installed in corporations, hospitals, schools, police departments, and even prisons, and released some videos as they were. This is a clear example of how easily an IoT hack can peek inside a sensitive organization. If you use an IoT password that is weak in terms of security, and do not upgrade the firmware of communication equipment such as a router that transmits command to IoT devices, or use unprotected network services, IoT devices will be easy prey for hackers.
Life-threatening exploitation beyond asset theft
Numerous cyber threats such as deep fakes, phishing attacks, malware, and ransomware are now not only hacking home network security cameras. Unauthorized access and intrusion are also potential risk factors, and as a result new laws are emerging. In Europe, the focus is mainly on the imposition of manufacturers' security obligations such as the ban on basic encryption on smart devices and equipment, while in Asian countries including Korea, structural solutions such as the application of encryption technology are being actively discussed.
Low-spec, low-power IoT device security needs
Unlike mobile devices that evolve into a single computer on their own, IoT devices range from high-performance devices such connected car to low-spec devices like a smart lamp that simply turn its power off and on. Therefore, there is a limit to applying a high-spec security solution that guarantees strong security to all low-spec, low-power IoT devices currently sold the most in the market. Accordingly, the demand for an IoT security solution that can cover even low-spec IoT devices is steadily increasing.
Solution
swIDch’s IoT Auth Platform OTAC provides a secure IoT communication environment by blocking the possibility of device hacking and control through dynamic codes that change each time they connect and command. Based on OTAC, a lightweight technology of less than 4KB, the OTAC Applet is embedded in the SIM card to implement strong end-to-end IoT authentication and control command protection that covers even low-spec IoT devices. In addition, it safely transports the control server command to the device to block the execution of various control commands that are not valid.
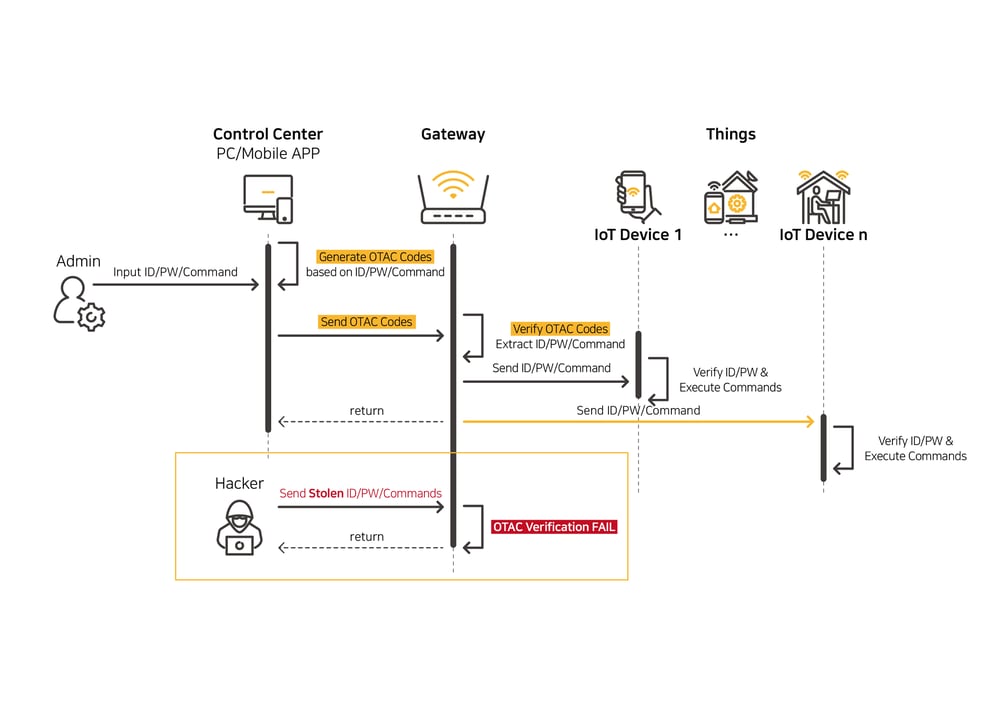
Device authentication and data integrity verification through OTAC capable of embedding to SIM card
swIDch’s IoT Auth Platform OTAC passes through the process of verifying data through the OTAC Applet embedded in the SIM card and firmware, and delivers the server's command to the IoT device safely and quickly. Currently, most IoT systems use a fixed value or unencrypted plaintext to pass a command. In addition, since there is no step that acts as a security gateway between the control and the device, if the command is stolen, the IoT device can be controlled by an unauthorized system. swIDch generates a different OTAC for each device every cycle, authenticates the device, and secures data integrity by verifying that the data is invalid if the transmitted data during OTAC generation is tampered with.
[As is] IoT device control problem by unauthorised system
[To-be] IoT security system using SIM card with OTAC Applet embedded
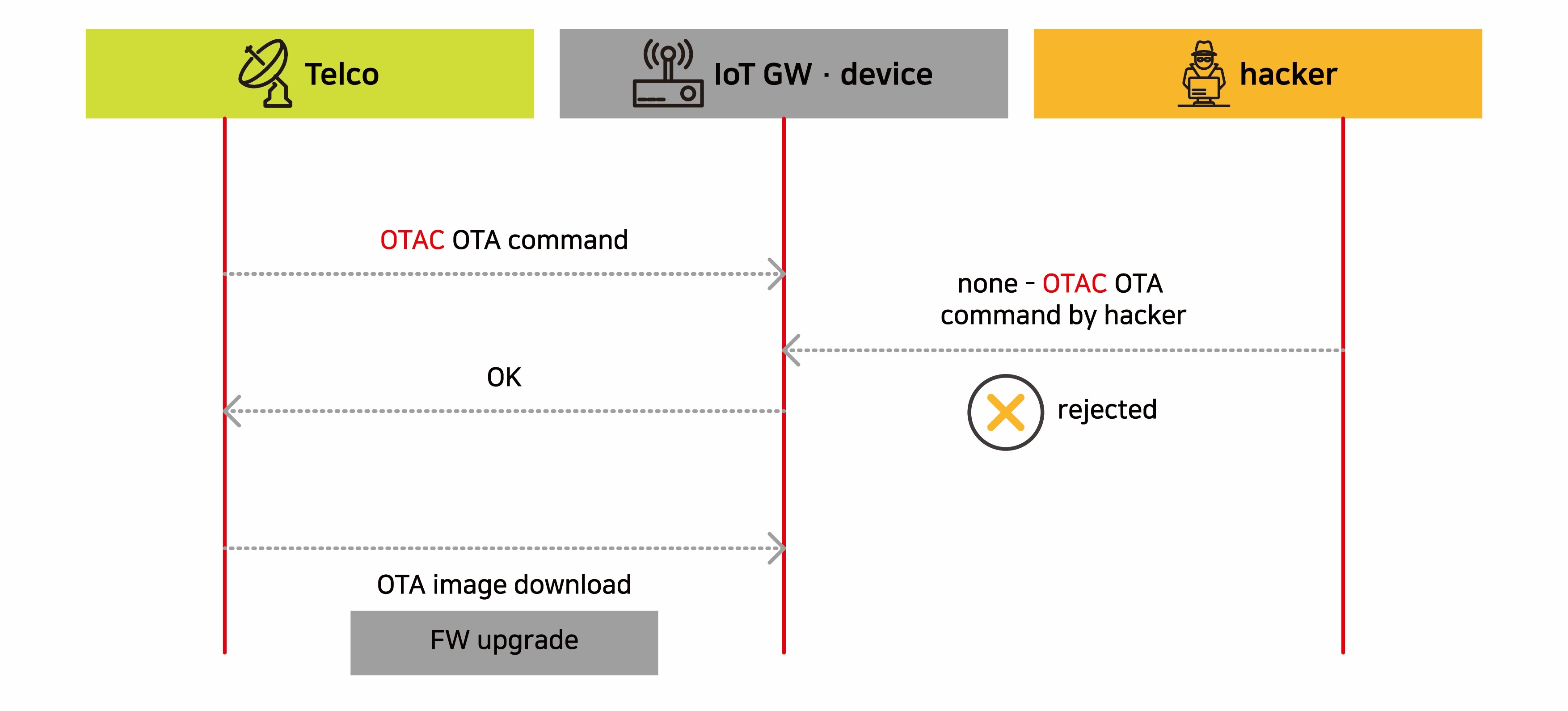
Implement a secure IoT device firmware upgrade
Recently, hackers who attack IoT devices often manipulate the device firmware to download illegal firmware or plant malware on the device. swIDch uses hashes of firmware files as a seed when generating OTAC to verify and execute only OTA commands sent from valid IoT servers. Therefore, since the download command from the unauthorized system itself is not approved by the device, it can naturally block the occurrence of illegal software downloads.
Improved security by linking with VPN, PSK-TLS, etc.
swIDch’s IoT Auth Platform OTAC is not only used for IoT device authentication and data integrity but also can be used together for device authentication for new VPN connections and connection maintenance. Also, by using the OTAC generated for authentication and integrity assurance as a dynamic key that reinforces the fixed pre-shared key (PSK) of PISK-TLS, you can secure a lighter and higher level of confidentiality than current high-spec security layered system.
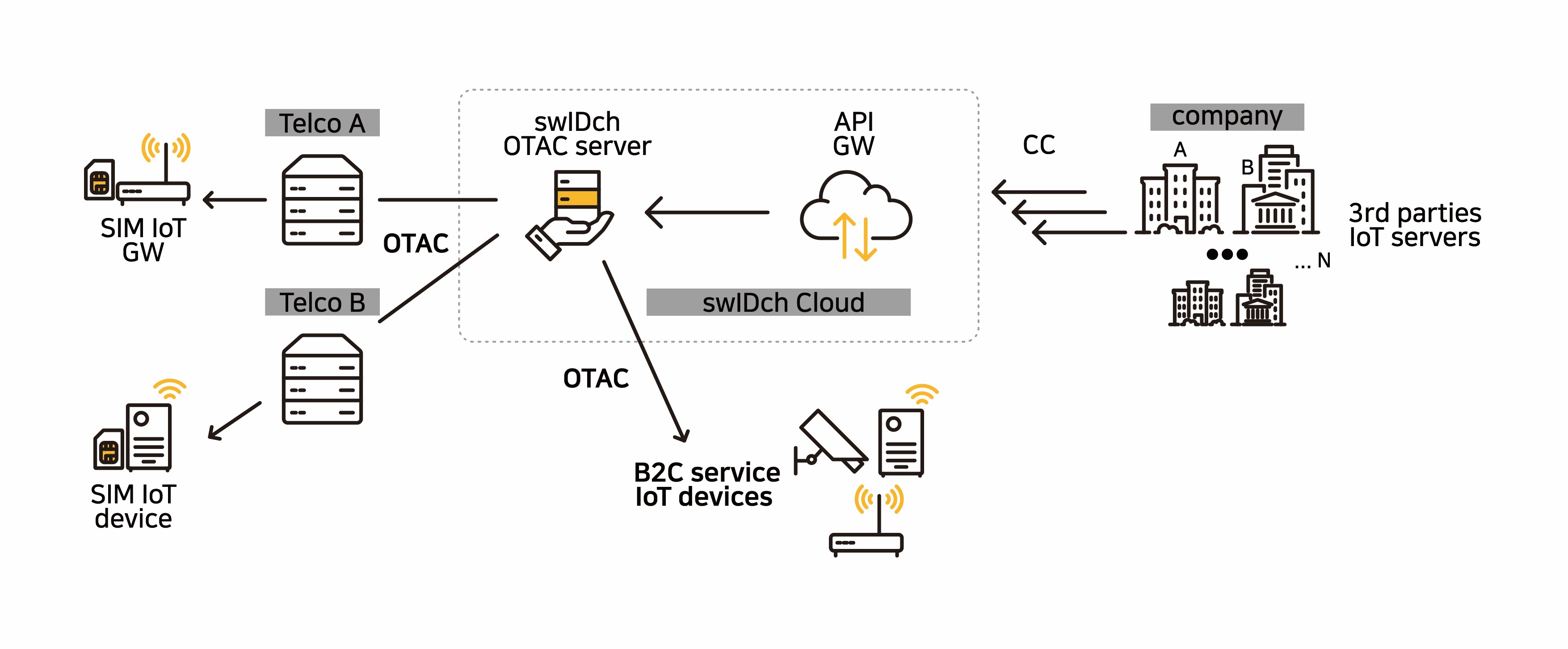
Supports both on-premise and cloud services
swIDch provides an on-premise service that provides the OTAC system to telecommunication operators and installs it on-premise, and a cloud service that raises the OTAC server and API gateway to the cloud.
On-premise service
The OTAC system built on-premise allows telecom operators to provide additional security products other than virtual private networks (VPNs) as additional services. It can be used as a service to secure new subscribers and create revenue sources by adding it as an option to the current IoT line plan itself.
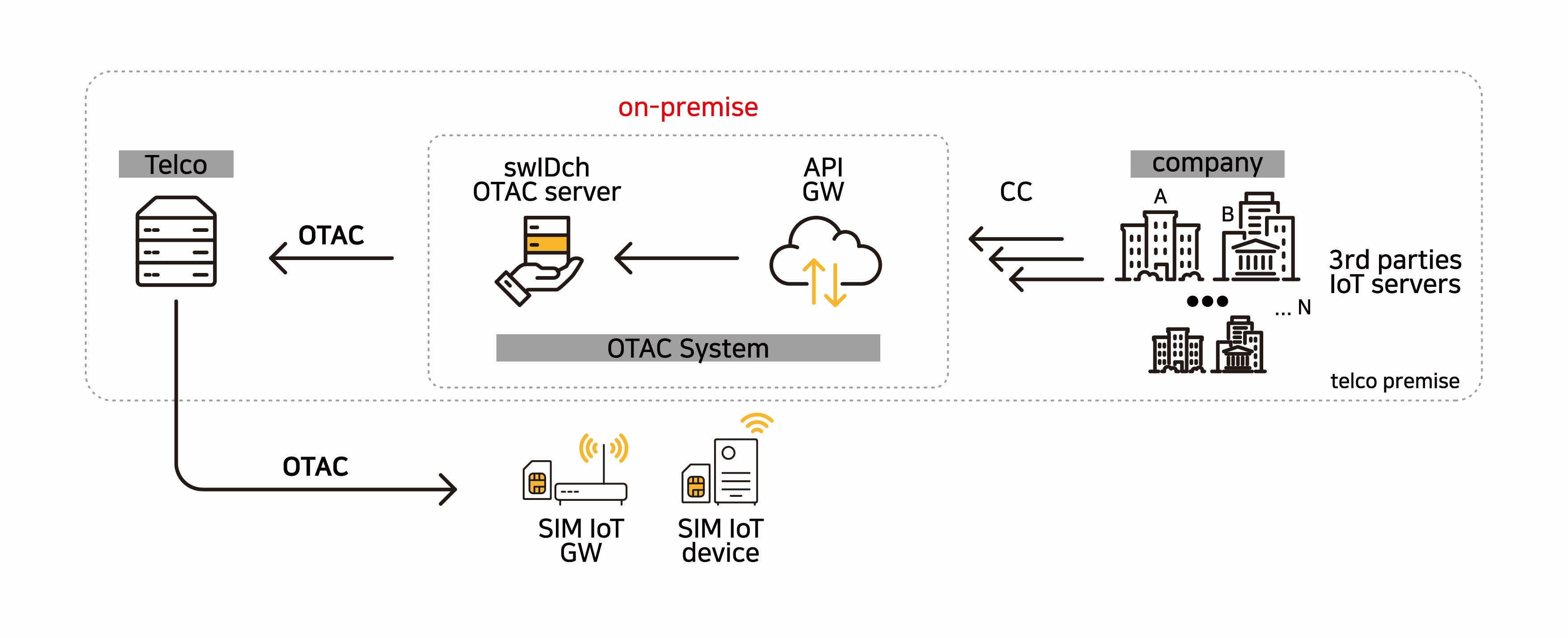
Cloud service
Telecom operators can use the IoT auth platform OTAC through the cloud service provided by swIDch without building their own OTAC system. swIDch provides OTAC APIs to IoT device companies that provide IoT services of the telecommunication service providers.
Benefits
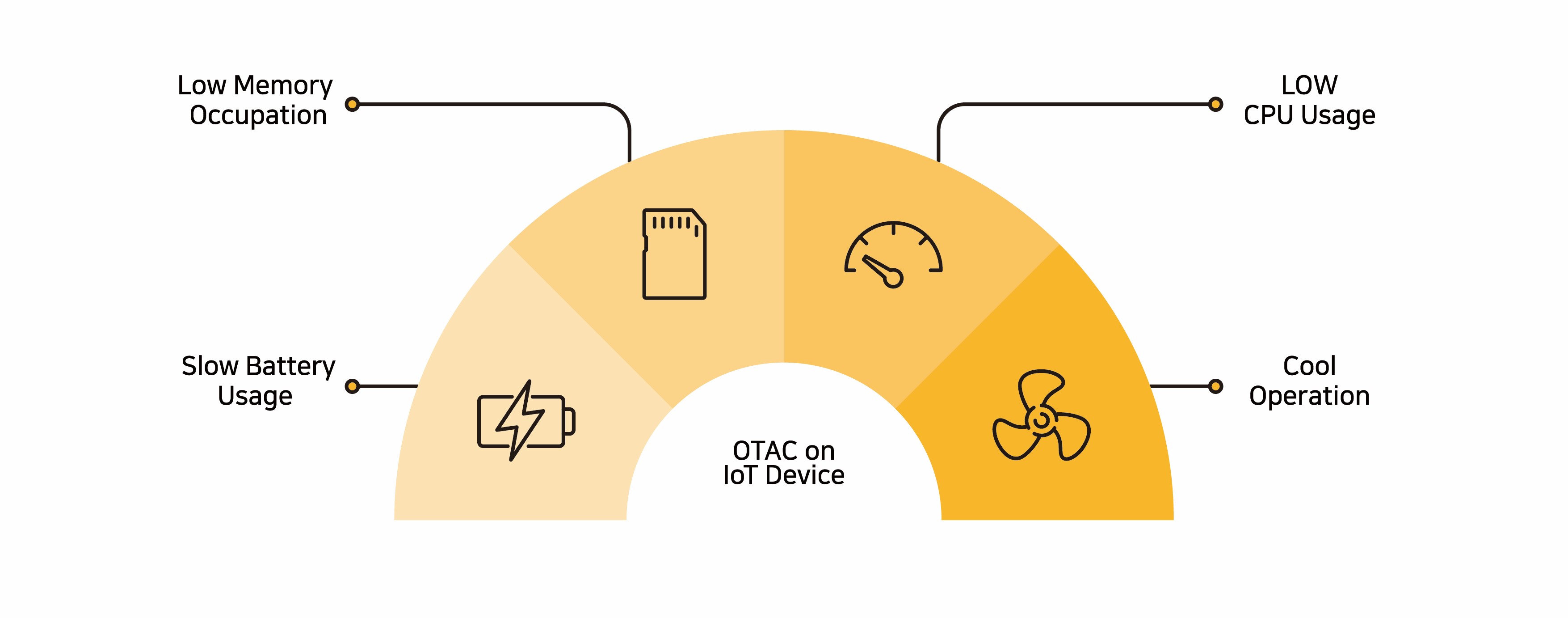
Sustainability and high availability (HA) are critical keywords that underpin the products, services, and consumption of this era. swIDch contributes to reduction in system construction and maintenance costs by reducing resource usage such as CPU and power through OTAC, a lightweight technology of less than 4KB, while shortening the time-to-market based on seamless integration, enabling telecom operators to provide new services quickly without failure or new infrastructure.
IoT authentication security system construction and maintenance cost reduction
OTAC is a lightweight technology of only 4KB, so it consumes very little CPU load or power. OTAC Applet embedded in a SIM card is an eco-friendly technology that uses only 20KB of memory. However, since it performs a security role similar to TLS required by IoT SAFE, it is possible to build a strong IoT authentication security system with fewer resources. In addition, it can be used as a cloud service without the need to build the system, which results in reduction of the initial deployment cost.
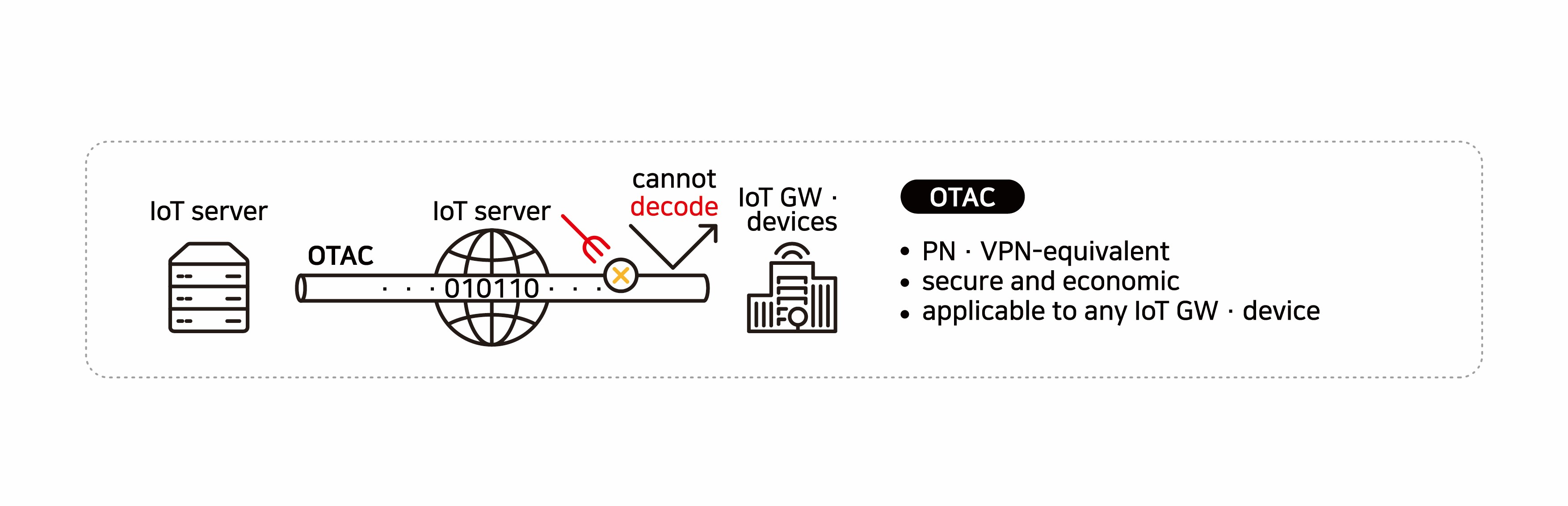
Expectation of new revenue as a complementary device to PN and VPN
As swIDch’s IoT Auth Platform OTAC provides a new solution to the security, computing resource, and cost problems of private networks and virtual private networks (VPNs), it is particularly suitable for the IoT industry that uses low power.
Since it can be applied as an inexpensive and lightweight security solution comparable to PN and VPN telecommunication operators can create new revenue models for IoT service providers who don’t require much video and data transmission or have cost-conscious clients.
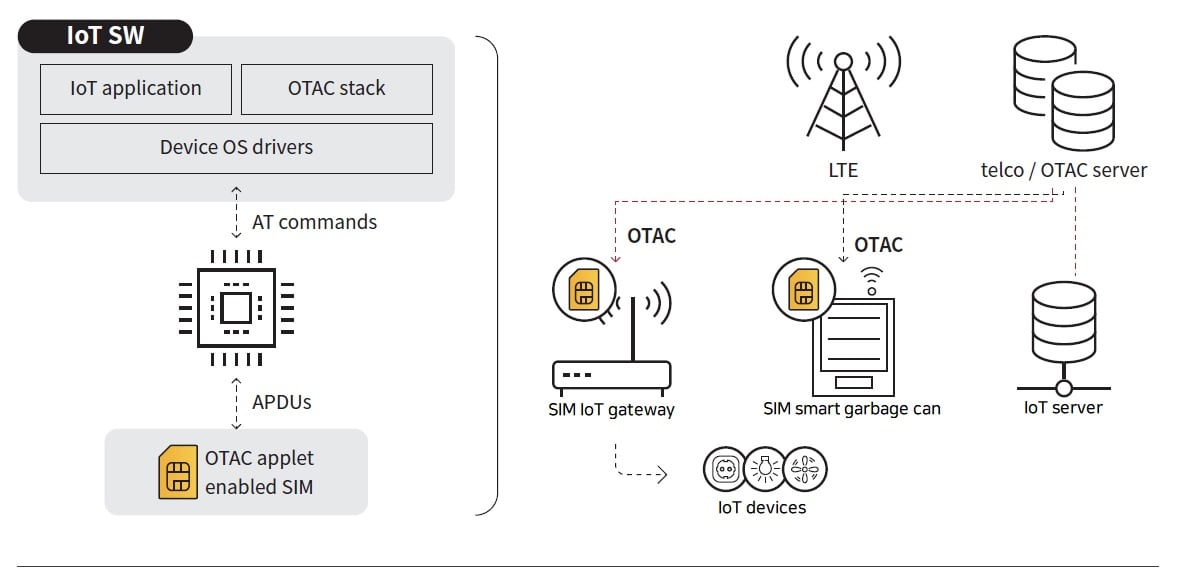
Accelerate time-to-market through easy integration
swIDch supports embedding the OTAC Applet in the SIM card from the start, but it also supports downloading or updating to SIM cards already in service. It accommodates not only regular SIM cards, but also eSIM (embedded SIM) and iSIM (integrated SIM), allowing multiple options for telcos and businesses alike. A SIM card embedded with the OTAC Applet is applied to communication equipment such as IoT gateways and routers or IoT devices that can be equipped with a SIM card, and is connected to the backend of the carrier through the LTE network, so the integration work is very simple. Also, the time to deployment and service launch can be shortened as it can be installed in the firmware of IoT devices or various mobile devices rather than the SIM card.
Contact us today
Why swIDch
that provides all of the following features, tested and substantiated
by the University of Surrey technical report
sufficient to IDENTIFY user
and AUTHENTICATION
off-the-network environment
Single-step identification and authentication with the code alone. Include our biometric option and get single-step MFA. Vastly improved UX by removing steps.
OTAC is a dynamic code, which means the code is constantly changing. Eliminates all use of static information. Forget usernames and passwords forever. Vastly reduced workload for IT helpdesks.
No network connection required for generating OTAC, enabling uninterrupted use no matter where you are. No more waiting for additional tokens/OTPs and no need for heavy public key infrastructure (PKI).
Highly configurable code parameters and lightweight SDK/applet means wide range of deployment options on many devices across multiple sectors.