Zero Trust Maturity Model: Transitioning to Zero Trust Architecture

In an era marked by escalating cyber threats and the transformative power of digital connectivity, the concept of security has undergone a paradigm shift. According to the Precedence Research, the global zero trust security market, with a size that reached USD 25.12 billion in 2022 and is projected to surge to around USD 118.5 billion by 2032, poised to grow at a CAGR of 16.78% during the forecast period from 2023 to 2032, has been propelled by a convergence of factors: the relentless evolution of cyberattacks, the imperative for improved security measures, and the expanding realm of cloud-based services.
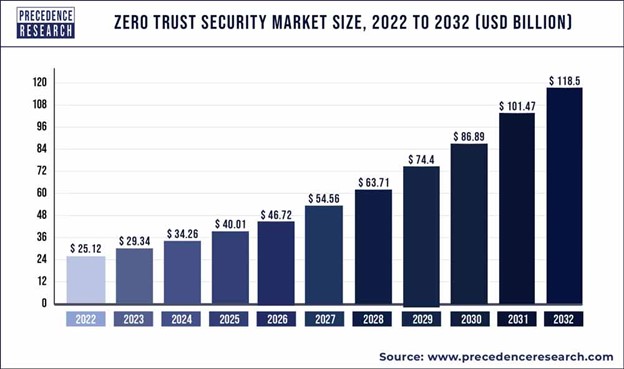
As organizations grapple with the need for comprehensive protection against ever-evolving cyber risks, the Zero Trust architecture emerges as the sentinel of safeguarding critical assets. This architecture's fundamental tenet, perpetual verification and authorization, resonates as a powerful response to the complexity of modern threats, charting a resilient path forward in a digital landscape characterized by uncertainty and interconnectivity. North America led the global market with the highest market share of 38% in 2022, underscoring the region's proactive stance in embracing this transformative approach to security.
Why Zero Trust?
Zero Trust is a modern approach to the evolving world of cybersecurity. It emphasizes the need to move away from a perimeter-centric network approach to a model focused on continuous authentication and assessment of Trust across every device, user and application.
Zero Trust security model was developed to assume no user or device is inherently Trustworthy and all access must be authenticated and verified. One of the core principles of Zero Trust is to assume there is a breach and try to minimize its impact. Zero Trust model does not require reliance on a secure network and instead focuses on identities, individual resources and data regardless of the user’s location.
Where to start?
There is no definitive answer to where you should start on your Zero Trust journey, as different organizations may have different priorities, challenges, and goals. However, a common approach is to begin with assessing your current security posture and identifying the gaps and opportunities for improvement. You can use the Zero Trust maturity model as a reference to evaluate your level of maturity across six key domains: identities, devices, applications, data, infrastructure, and networks.

Once you have a clear understanding of your current state and desired outcomes, you can create a roadmap and a plan for implementing Zero Trust in your organization. You can use the Zero Trust maturity model as a guide to help you define your vision, scope, objectives, metrics, and budget for your Zero Trust initiative. You can also leverage the best practices and lessons learned from other organizations that have successfully adopted Zero Trust.
Zero Trust maturity model
The Zero Trust maturity model is a framework that helps organizations assess their current level of security and plan their transition to a Zero Trust architecture. A Zero Trust architecture is a security model that assumes no user or device can be trusted by default, and requires strict verification and authorization for every access request to data and resources. The Zero Trust maturity model was developed by the Cybersecurity & Infrastructure Security Agency (CISA), a federal agency that provides cybersecurity guidance and services to the government and the private sector.
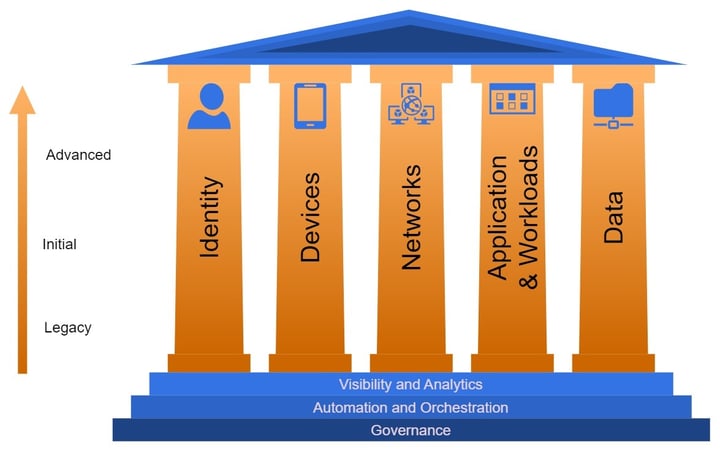
The Zero Trust maturity model consists of five pillars and three cross-cutting capabilities that cover the essential elements of security: identities, devices, applications, data, infrastructure, and networks. The pillars are based on the principles of Zero Trust, such as verifying explicitly, using least privilege access, assuming breach, securing data, and monitoring continuously. The cross-cutting capabilities are based on the enablers of Zero Trust, such as governance, automation, and visibility.
Zero Trust maturity journey
Different organizations may have different starting points and goals for their Zero Trust maturity journey, depending on their current security posture, business needs, and challenges. However, a common approach is to use a maturity model that provides a framework for measuring the current state and desired outcomes of Zero Trust implementation. A maturity model can help organizations identify the gaps and opportunities for improvement, prioritize the security efforts and investments, and track the progress and impact of Zero Trust solutions.
Below you’ll find a path to transition to a Zero Trust architecture for each of the pillars of the principles of Zero Trust.
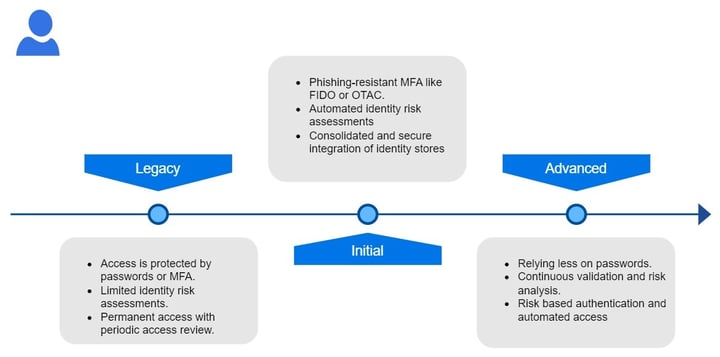
Identity
Enterprises should ensure and enforce user and entity access to the right resources at the right time for the right purpose without granting excessive access.
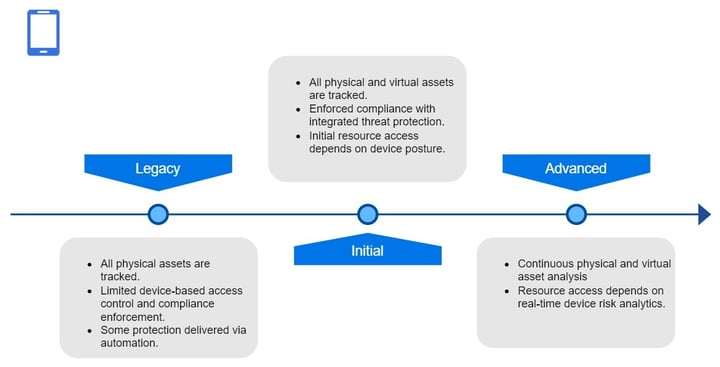
Devices
Enterprises should secure all devices, manage the risks of authorized devices that are not company-controlled, and prevent unauthorized devices from accessing resources. Device management includes maintaining a dynamic inventory of all assets including their hardware, software, firmware, etc., along with their configurations and associated vulnerabilities as they become known.
Networks
Zero Trust architecture enables a shift away from traditional perimeter-focused approaches to security and permits companies to manage internal and external traffic flows, isolate hosts, enforce encryption, segment activity, and enhance enterprise-wide network visibility.
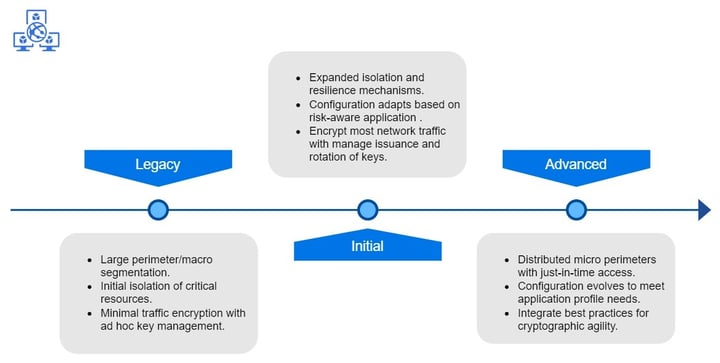
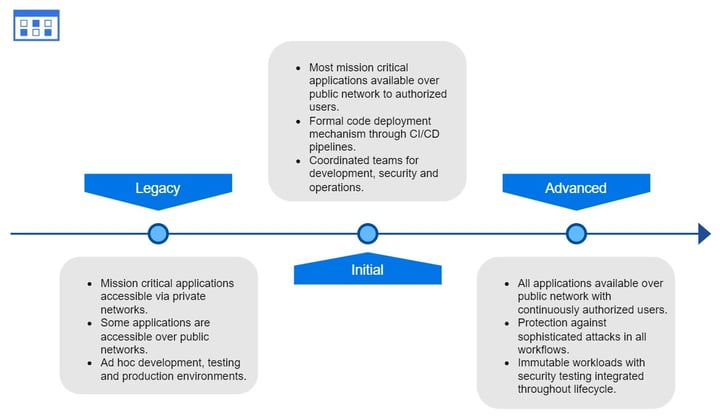
Applications & Workloads
Companies should manage and secure their deployed applications and should ensure secure application delivery. Granular access controls and integrated threat protections can offer enhanced situational awareness and mitigate application-specific threats.
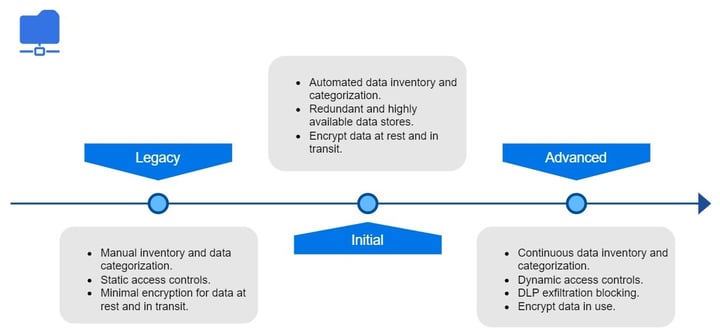
Data
Company data should be protected on devices, in applications, and on networks. Companies should do inventory checks, categorize, and label data; protect data at rest and in transit; and deploy mechanisms to detect and stop data exfiltration.
Conclusion
A Zero Trust security model is a framework that assumes no user or device can be trusted by default, and requires strict verification and authorization for every access request to data and resources. A Zero Trust security model aims to reduce the risk of cyberattacks, data breaches, and insider threats by following the principles of verifying explicitly, using least privilege access, assuming breaches, securing data, and monitoring continuously
The Zero Trust maturity journey is not a one-time project, but rather a continuous and iterative process that involves assessing, planning, deploying, and evaluating Zero Trust solutions. Finally, you can choose the right technologies and solutions that can help you achieve Zero Trust in your organization. You can explore the various offerings from various vendors that can help you implement Zero Trust across identities, devices, applications, data, infrastructure, and networks.
--------------------

Author: Vinny Sagar, Solution Architect, swIDch
With over 15 years of experience in pre-sales, consulting and software development in the Identity and Cyber Security space Vinny has helped many clients across various industries and regions to design and deploy Zero Trust solutions that meet their specific needs and challenges.
--------------------

swIDch will continue its quest to innovate and pioneer next-generation authentication solutions. To stay up-to-date with the latest trends sign up to our newsletter and check out our latest solutions.

The distributed control system (DCS) is the core of industrial automation. It synchronises critical operations in power

In the age of digital transformation, cybersecurity has become a boardroom topic across industries. But while IT

The ubiquity of Public Key Infrastructure (PKI) in securing our digital world is undeniable. From the padlock icon in
Looking to stay up-to-date with our latest news?