Tackling Authentication Vulnerabilities in OT Devices Beyond PLCs

Operational Technology (OT) devices, including SCADA systems, Distributed Control Systems (DCS), Remote Terminal Units (RTUs), and Human-Machine Interfaces (HMI), play a vital role in critical infrastructure, such as energy grids, water treatment facilities, and national defence systems. Unfortunately, their vulnerabilities are increasingly exploited by hackers, posing serious risks to public safety and essential services.
Why OT Devices Attract Hackers
Hackers target OT devices for several reasons:
- High-Impact Results: A successful breach can disrupt vital services, making OT systems appealing for ransomware, sabotage, or terrorism.
- Outdated Security: Many systems still rely on default or static passwords, rarely updated, making them easy targets compared to modern IT networks.
- Gateway to Wider Networks: OT devices often serve as entry points for hackers to access interconnected systems.
- Limited Monitoring: A lack of sophisticated monitoring tools means attackers can go undetected for longer periods.
How Hackers Exploit OT Systems

Attackers exploit weak security measures and outdated practices to devastating effect. Static passwords are often the starting point, providing easy access to systems. Once inside, they can move laterally to manipulate devices, disrupt operations, or extract sensitive data.
Consider these real-world examples:
- SCADA and Water Systems: Oldsmar, Florida Water Treatment Attack
In 2021, a hacker used TeamViewer to access the SCADA system of a water treatment plant in Florida, attempting to increase sodium hydroxide levels to toxic amounts. Shared static passwords and insufficient network segmentation made the attack possible. A quick-thinking operator averted disaster, but the incident underscored the dangers of poor security practices. - RTUs and Pipelines: Ransomware Attack on a Natural Gas Facility
In 2020, ransomware disrupted a natural gas pipeline in the US for two days. Hackers exploited weak security in RTUs at remote facilities, halting communication between SCADA systems and field devices. This showed how vulnerable edge devices can cause widespread disruption across supply chains. - DCS and Power Grids: Ukraine Power Grid Attack
In 2015, hackers infiltrated Ukraine’s power grid using stolen credentials obtained via spear-phishing. They disabled circuit breakers and launched denial-of-service attacks, cutting power to over 230,000 residents during winter. This attack demonstrated the cascading consequences of compromised DCS systems.
Lessons from Past Attacks
These incidents highlight the urgent need to replace static passwords with robust authentication solutions. Default credentials are easy targets for hackers, who can steal or brute-force them with minimal effort.

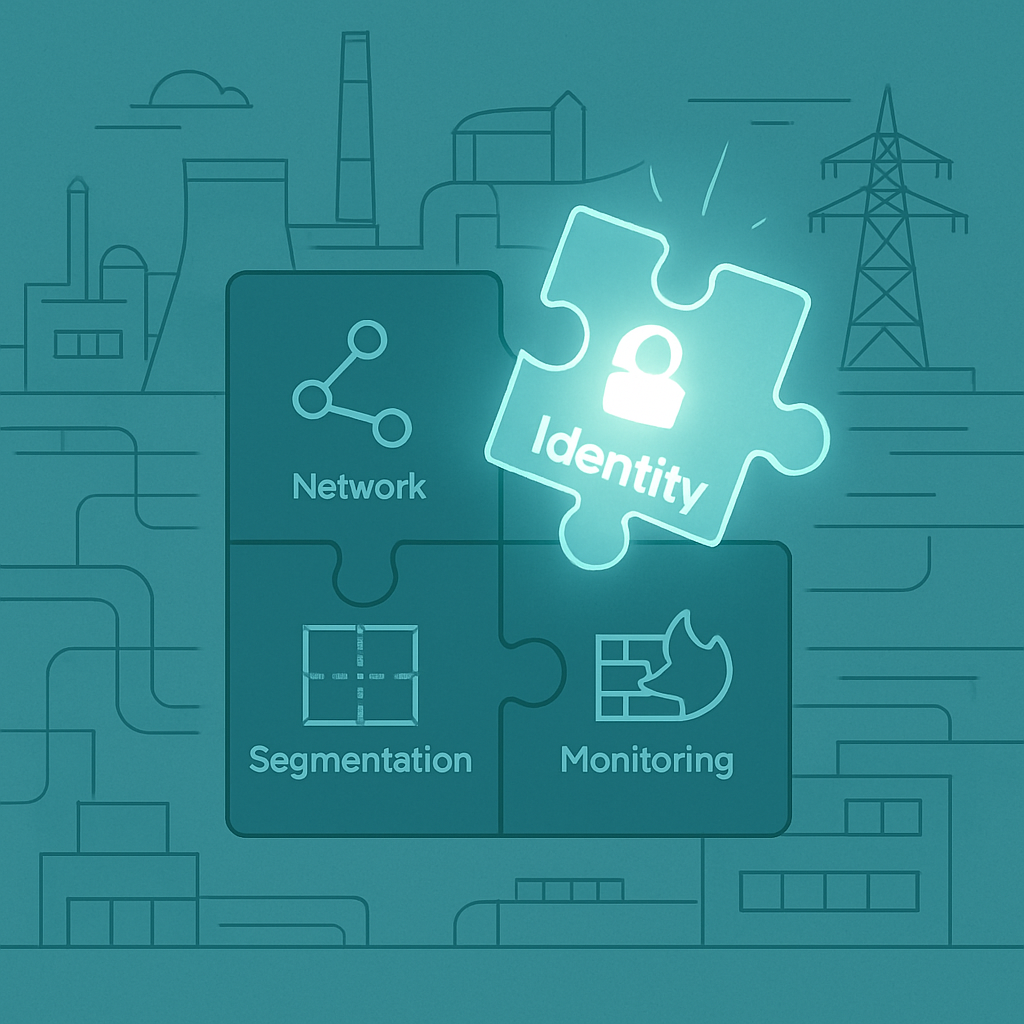
But stronger authentication is only part of the solution. To protect OT systems effectively, organisations should:
- Implement Dynamic Authentication: Replace static passwords with one-time codes or multi-factor authentication (MFA).
- Segment Networks: Isolate critical OT devices to prevent intrusions from spreading.
- Apply Regular Updates: Patch software and firmware to close known vulnerabilities.
- Enable Continuous Monitoring: Use real-time anomaly detection to identify and address suspicious activity early.
Moving Towards Safer OT Systems
As OT devices evolve, so must the strategies to secure them. The interconnected nature of these systems means a breach in one device can ripple across entire networks, with far-reaching consequences. Proactively adopting dynamic authentication and robust security measures is essential to safeguarding critical infrastructure.
With OT systems underpinning so much of our modern life, there’s no time to delay. Addressing vulnerabilities now will ensure these essential services remain safe and reliable in the future.
--------------------

swIDch will continue its quest to innovate and pioneer next-generation authentication solutions. To stay up-to-date with the latest trends sign up to our newsletter and check out our latest solutions.

The OT and critical infrastructure incidents we witnessed throughout 2025 showed, with unusual clarity, where attackers

2025 was marked by a series of real-world OT and infrastructure incidents across Europe and North America. A dam gate
Even after a year filled with operational technology (OT) security investments, audits, and framework updates, one
Looking to stay up-to-date with our latest news?