Safeguarding Communication in the Age of Quantum Computers

Quantum computers represent a paradigm shift in computation, leveraging the unique properties of quantum mechanics to tackle problems that classical computers cannot. As quantum technology advances, we are on the brink of a new era in computing.
Regular computers process information using bits, which can be either 0 or 1. Quantum computers leverage the strangeness of quantum mechanics with qubits. These qubits can be 0, 1, or both at the same time (superposition). This lets them explore multiple possibilities simultaneously.
Imagine a maze. A regular computer checks each path one by one. A quantum computer explores all paths at once, therefore finding the solution much faster (as illustrated in this diagram below: Figure 1). This makes them more powerful for certain tasks like drug discovery or breaking modern encryption (which is why securing communication & authentication is crucial).
%20VS%20Quantum%20computer%20(combined).png?width=720&height=443&name=Classical%20computer%20(left)%20VS%20Quantum%20computer%20(combined).png)
Figure 1: Classical computer (left) VS Quantum computer (right). Quantum computer are much faster for certain problems
Why quantum computers are a threat to digital communication
Encryption algorithms like RSA and Diffie-Hellman are built upon mathematical problems (prime numbers) that become incredibly complex as the size of the key increases. To break these algorithms requires trying every possible combination, taking traditional computers an impractical amount of time for large keys.
As explained above, quantum computers utilize qubits to provide an exponential increase in compute speed for solving specific problems, crucial to breaking modern encryption algorithms.
A specific algorithm, Shor's algorithm, has been created for use by quantum computers to break modern encryption algorithms. This algorithm can break the encryption used in current communication protocols significantly faster compared to traditional computers.
If you would like to understand more in detail why and how quantum computers are a threat to digital communication I would recommend watching this video on YouTube: How Quantum Computers Break The Internet... Starting Now
Store Now Decrypt Later (SNDL)
Store now, decrypt later (SNDL), also known as harvest now, decrypt later (HNDL), refers to a surveillance strategy which involves:
- Acquiring encrypted data: This data could be intercepted communications, files, or other information protected by encryption algorithms.
- Storing the encrypted data: This data is then stored for a long period, potentially for years or decades.
- Decrypting the data later: The idea is that the data will be decrypted at a future time, when advancements in decryption technology make it possible.
The primary concern behind SNDL is the potential threat posed by quantum computers. These powerful machines are still under development, but they have the theoretical capability to break the encryption used in many current communication protocols much faster than traditional computers.
Here's why SNDL is a concern:
- Forward-thinking adversaries: Actors like nation-states or cybercriminals might intercept and store encrypted data today, hoping to decrypt it later with the help of future breakthroughs in quantum computing.
- Long-term security risk: Even if current encryption methods are considered secure today, their effectiveness cannot be guaranteed in the future due to the potential of advancements like quantum computers.
Should we be worried?
Not yet, SNDL is still a theoretical concept: There's no concrete evidence of its actual use in the real world. Quantum computing is still in its early stages: while the potential threat exists, it's uncertain when or if quantum computers will become powerful enough to break current encryption methods on a large scale. Their practical implementation faces challenges related to stability, error correction and scalability.
Quantum computers leverage the strangeness of quantum mechanics with qubits. It only takes a few thousand perfect qubits to break RSA encryption. But the qubits we have today are imperfect, so additional qubits are needed to act as redundant information.
In 2012 it was estimated it would take 1 billion qubits to break RSA encryption, however in 2019 that number plumbitted to just 20 million qubits. If we look at the state of IBM’s quantum computers, we are nowhere near to the required number of qubits to break encryption, but progress seems exponential; it will be only a matter of time for the qubit required vs qubit available numbers to converge (as illustrated in this graph below: Figure 2) before all encryption and digital communication can be broken.
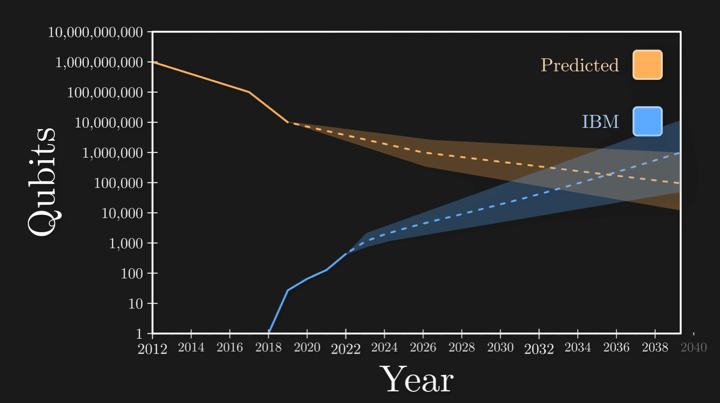
Figure 2: Prediction of when quantum computers will be powerful enough to break RSA encryption.
Source: Veritasium How Quantum Computers Break The Internet... Starting Now
Quantum-safe algorithms
As development in quantum computers grows exponentially, a potential threat looms: the ability to crack current encryption methods used in online communication and authentication. This is where quantum-safe algorithms step in, offering a shield against this future challenge.
Quantum-safe algorithms, also known as post-quantum cryptography (PQC) algorithms, are a new breed of cryptographic tools designed to be resistant to attacks from both traditional and quantum computers.
How are they different?
Quantum-safe algorithms are built on different mathematical foundations to traditional algorithms. They utilize entirely new problem sets that are believed to be difficult for both traditional and quantum computers to solve efficiently. This ensures a higher level of security in the face of potential advancements in quantum computing.
|
Note: Apple recently announced a security upgrade in iMessage with the introduction of PQ3, a groundbreaking post-quantum cryptographic protocol that advances the state of the art of end-to-end secure messaging. With compromise-resilient encryption and extensive defenses against even highly sophisticated quantum attacks. Source: https://security.apple.com/blog/imessage-pq3/ |
Is OTAC quantum safe for authentication?
One-Time Authentication Code (OTAC) is based on and improves upon TOTP (Time-Based One-Time Password). Quantum computers have the potential to break certain cryptographic algorithms, including those based on integer factorization (e.g., RSA) and discrete logarithms (e.g., Diffie-Hellman). However, TOTP relies on hash functions (such as SHA-1 or SHA-256) and symmetric encryption (HMAC), which are not directly vulnerable to quantum attacks. TOTP remains secure when combined with a strong random secret though the real-world security of OTAC depends on the security practices of the OTAC application and the protection of the secret.
To make sure OTAC is quantum safe we recommend encrypting the secret with a quantum safe algorithm.
Navigating Quantum Threats to Secure Our Digital Future

While the potential threat of quantum computers breaking current encryption methods is real, there is no immediate need for widespread panic. Quantum computing is still in its early stages and experts estimate it could be several years, or even decades, before it poses a significant threat to widely used encryption algorithms.
However, proactive measures are crucial. The development of post-quantum cryptography (PQC) and staying informed about advancements in quantum computing are essential steps to ensure the long-term security of our communications. By taking these steps now, we can be prepared for the future and ensure our sensitive information remains protected, even in the face of potential technological disruptions.
Remember, security is an ongoing process, not a one-time fix. Staying vigilant and adapting to new threats are essential for safeguarding our digital world.
--------------------

Author: Vinny Sagar, Solution Architect, swIDch
With over 15 years of experience in pre-sales, consulting and software development in the Identity and Cyber Security space Vinny has helped many clients across various industries and regions to design and deploy Zero Trust solutions that meet their specific needs and challenges.
--------------------

swIDch will continue its quest to innovate and pioneer next-generation authentication solutions. To stay up-to-date with the latest trends sign up to our newsletter and check out our latest solutions.

When people think of cyberattacks, they often picture stolen data, financial fraud, or personal privacy violations.

In the realm of Operational Technology (OT), the security measures applied to protect critical infrastructure systems

In the world of Operational Technology (OT), firmware updates are a necessary but often overlooked aspect of
Looking to stay up-to-date with our latest news?