(Part 3) Key security vulnerabilities in IoT environment and how to effectively counteract them
Join me, Charlie Choi, for Part 3 of our Key IoT Vulnerabilities series, with a focus on OWASP IoT Top 10.
6. Insufficient Privacy Protection
User’s personal information stored on the device or in the ecosystem that is used insecurely, improperly, or without permission.
For example, the facial recognition technology market is growing rapidly and the technology is widely used. However, there’re privacy concerns that comes with misuse of biometrics and facial recognition data and improper data storage and sharing.
One related story comes from Facebook. The company is backing away from facial recognition because experts and activists have warned this technology is plagued with bias and privacy problems
 Figure. Facebook's metaverse
Figure. Facebook's metaverse
7. Insecure Data Transfer and Storage
Lack of encryption or access control of sensitive data anywhere within the ecosystem, including at rest, in transit, or during processing.
For example, IoT devices need to be lightweight so they’re using MQTT and COAP protocol.
When it comes to MQTT, IT is used to send sensor data.
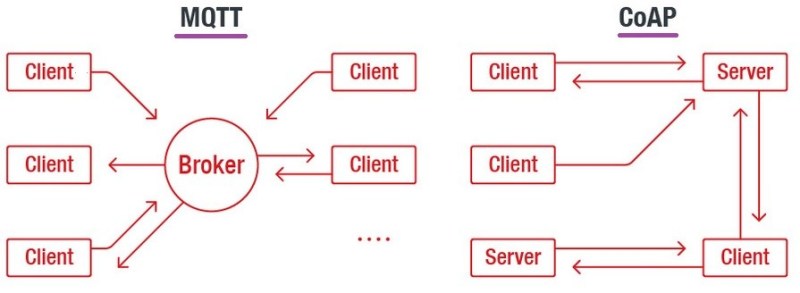 Figure. MQTT and CoAP protocol
Figure. MQTT and CoAP protocol
CoAP is also standardized to send and receive sensor data. They send plaintext data over the wire by default.
In order to address the issue, TLS is used to encrypt data in transit and to authenticate the IoT devices to the application. However, TLS isn’t lightweight. IoT devices run on low power chips which may only have 256 or 512 KB of RAM and they transact lots of small information constantly without as much overhead as possible to save RAM and battery life.
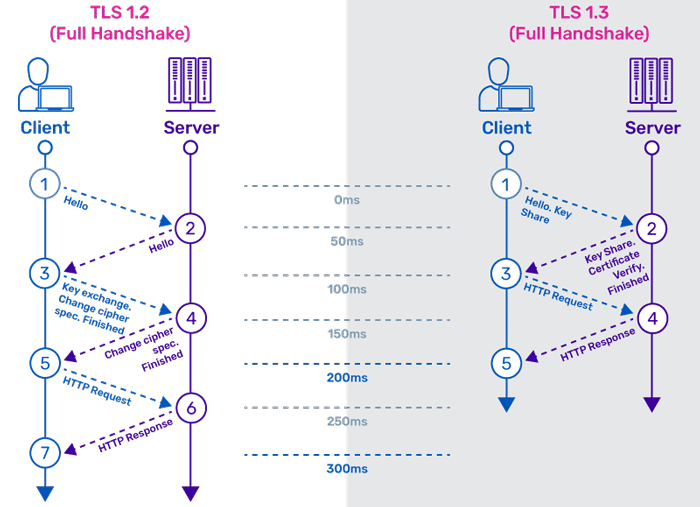
Figure. TLS handshake
8. Lack of Device Management
Lack of security support on devices deployed in production, including asset management, update management, secure decommissioning, systems monitoring, and response capabilities.
 Figure. Major challenges to IoT technology
Figure. Major challenges to IoT technology
According to the research on IoT trends, Major challenges to IoT technology are as follows.
In addition to this, another major challenge is down to the fact that half of IT departments do not change default passwords.
You can look up IoT device default password.
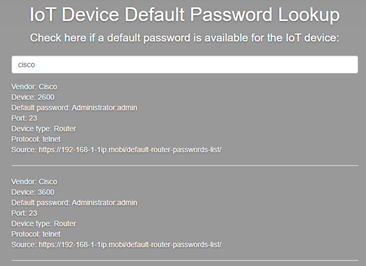
Figure. IoT device default password lookup
9. Insecure Default Settings
Devices or systems shipped with insecure default settings or those lacking the ability to make the system more secure by restricting operators from modifying configurations.
For example, IoT devices are shipped with default, hard-corded configuration that are an easy target for hackers.
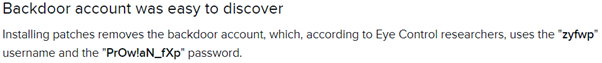
The example below shows a VPN gateway which contains a hard-coded admin-level backdoor account.
Figure. The device shipped with backdoor account by default
10. Lack of Physical Hardening
Lack of physical hardening measures, allowing potential attackers to gain sensitive information that can help in a future remote attack or take local control of the device
Physical access to IoT devices can be put at risk if they are not hardened against physical attack.
Deployment in poorly secured zone can subject the device to hacking including illegal access, theft of device etc.
--------
Thanks for reading. Part 4 coming soon...
About Charlie Choi
Charlie Choi is a technical director and a security advisor at SSenStone. He's been working in security consulting, application security and cloud security for over 20 years during which he has authored several books and a multiple expert papers. He has a Master of Industrial and information engineering from Soongsil University, Korea.
Looking to stay up-to-date with our latest news?